SEARCH
CATEGORIES
SUBSCRIBE
FOLLOW US
RECOMMENDED READING

Are you SaaS ready?
SaaS (Software as a Service) is flourishing. More and more companies are turning to SaaS and other on-demand solutions to respond to business needs faster and more cheaply. SaaS is a software delivery model in which software and associated data are centrally hosted on...

How to justify IT projects to your CFO
This article is based on a series of three blog posts I wrote entitled "How to justify Application Modernization to your CFO." Very similar cost/benefit justification principles apply to other IT projects, such as supporting users with mobile technology, extending...

12-Point Mobile Application and Data Security Checklist
In today’s 'always on' environment, both consumers and employees seek quick and immediate access to information when they want, wherever their location may be. According to recent report by Chief Marketer [1], mobile marketing budgets have increased [2] in the last 12...

What’s old is new again
Guest Blogger: Tom Mavroidis, president of NTM Consulting Incorporated As part of Tom’s portfolio he manages the Computer Department for ITWAL Limited, Canada’s national network of independent distributors. In this article Tom shares how multiple vendors worked...

Part 3: Putting Mobile Applications & Data Security In Perspective
This week concludes my series on Mobile Applications & Data Security. I'll leave you with tactics on how to secure application access to data and provide insight on how to secure communication between a mobile device and server. Ready? Let's dive in. One of the...

Part 2: Putting Mobile Applications & Data Security In Perspective
Did you know approximately 30% of mobile users save their password in the notes apps on the phone? And 264 mobile thefts were reported every day in 2012? These are just a few statistics I highlighted last week in my Putting Mobile Applications and Data Security In...

Part 1: Putting Mobile Applications & Data Security in Perspective
Today, many organizations are rushing to build mobile applications and mobile websites to gain a competitive advantage within their industry. The rate and speed at which applications are being pushed into the marketplace is phenomenal and is only increasing with the...
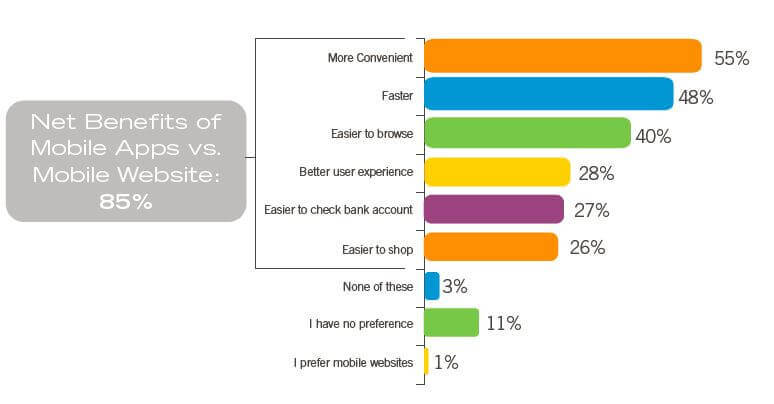
Mobile eCommerce – Join the Revolution!
Is “going mobile” on your company’s radar? If not, it should be because the mobile revolution is growing at an extraordinary pace. The number of smartphone users is rapidly rising – 42% a year, globally, according to research from Morgan Stanley. At this rate more...

Big-Bang Theory, Frankenstein, Darwinism – Which Strategy Is Right For You?
When you are faced with the mission to modernize your legacy business applications, there may seem like countless options to choose from. This assignment can be very intimidating, so take a deep breath and let's explore your options. Legacy Applications – Asset or...
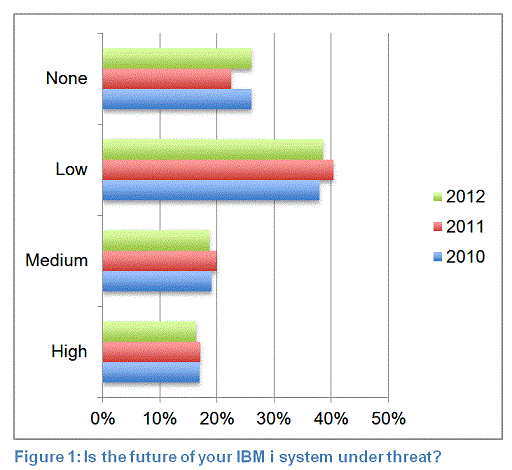
iPulse 2012 Results
The 3rd annual iPulse Survey, organized by LANSA, ran during November and December 2012 and was promoted to the global IBM i community via email, social media and publicized by leading industry media organization - IT Jungle. This year’s survey attracted just over...

The State of Mobile on IBM i
There’s no escaping the rapid pace of our evolving mobile world – including the ensuing demand for mobile apps – and businesses can’t afford to take a back seat when it comes deploying mobile solutions. If you’re an IBM i organization considering taking the dive into...

Go Native without the Pain
Guest Blogger: Paul Conte, President PCES, is a leading Application Development Strategist. My wife and I just got back from three weeks in the southwest of France; and when we travel, we like to go “native.” In this region of France that means a daily diet of duck,...
